Achieve significant savings faster with intelligent usage metering
Asset Vision™ is a SaaS-based IT asset intelligence solution that provides discovery, normalisation and usage metering in a fast and accurate basis for targeted cost savings and ongoing IT cost optimization. Asset Vision gathers highly granular usage data to identify software that is under-utilised or entirely unused. This can drive remove/recycle workflows, which quickly and measurably cut the costs of software licensing and maintenance.
By using the latest cloud technologies to bring you a future-proof, cost effective platform, it is available through a public cloud service running within the Amazon region closest to your location, providing the most secure option for your organization.
-
 Import and Integrate
Import and Integrate - Asset Vision provides a wealth of integration options for importing inventory data from other systems, including purchasing systems, service desks, and more. Building integrations is easy. An intuitive wizard walks you through the various steps to build and test an integration model. Once built, the model can be run on demand, or scheduled according to your needs.
-
 Business Intelligence
Business Intelligence - Business Intelligence is central to the Asset Vision platform with pre-configured dashboards, reports and data views are standard within the product. However, it is impossible to anticipate the reporting and data presentation needs of all organizations with complex IT environments, so the product was designed to enable IT professionals to craft answers to any questions that may emerge thru custom reporting. By collecting and processing data from every corner of the IT estate, this business intelligence capability ensures IT asset intelligence can be curated to meet your needs.
-
 Normalization and Enrichment
Normalization and Enrichment - At its core Asset Vision has an integrated, cloud-based and crowd-sourced recognition engine. This facility enables us to normalize virtually any meaningful IT asset data point. With over 1,500,000 total entries, Asset Vision is rarely unable to correctly identify and categorize IT asset data. In conjunction with our customers, we generally add over 1000 additional entries each quarter. In addition to simple recognition and normalization, our catalog has extensive enrichment. Data such as release dates, end of life dates, license metrics, location data, and more all combine to enrich the raw data returned by discovery into meaningful and actionable IT asset intelligence.
-
 Custom Fields
Custom Fields - Asset Vision provides for custom field creation, either within entirely new objects or extending existing objects. Once defined, customization survives all platform updates and can be incorporated into any of the business intelligence functions. If you need to record asset information unique to your organization, whether manually or automatically, Asset Vision IT asset management products will do the job.
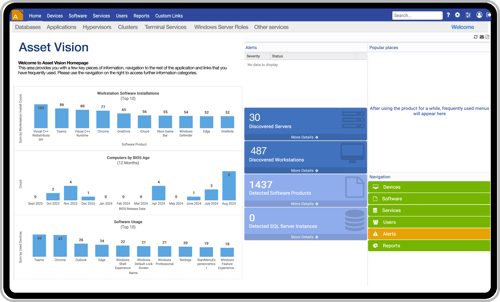
Asset Vision - Workstation
Asset Vision Workstation is designed to be the single source of truth for IT Assets—the definitive IT Asset Register. Flexible import mechanisms enable disparate sources of information to be easily added. You can integrate data from common sources of information such as SCCM then validate and reconcile with Asset Vision’s integrated asset discovery capabilities. You can then correlate the discovered information with procurement data such as Purchase Orders, Warranties, Advance Ship Notices, and Invoices from various sources.
The information is enriched and normalized with data elements such as location data and end of life dates, all backed by a team of Scalable data researchers who ensure high standards of data quality. Integrated search, reporting, and analytics means the information maintained by Asset Vision can be mined and shared with ease.
Optimize financial management with usage metering
Asset Vision Workstation is the ultimate in software usage metering technology. It delivers forensic-level usage analysis of traditional and virtual applications, applications running on virtual desktops and web applications. In conjunction with other core features of the Asset Vision solution, this can dramatically drive down operational IT costs by identifying hardware and software assets that can be reconfigured, recycled, or retired, so you can eliminate unnecessary expenditures.

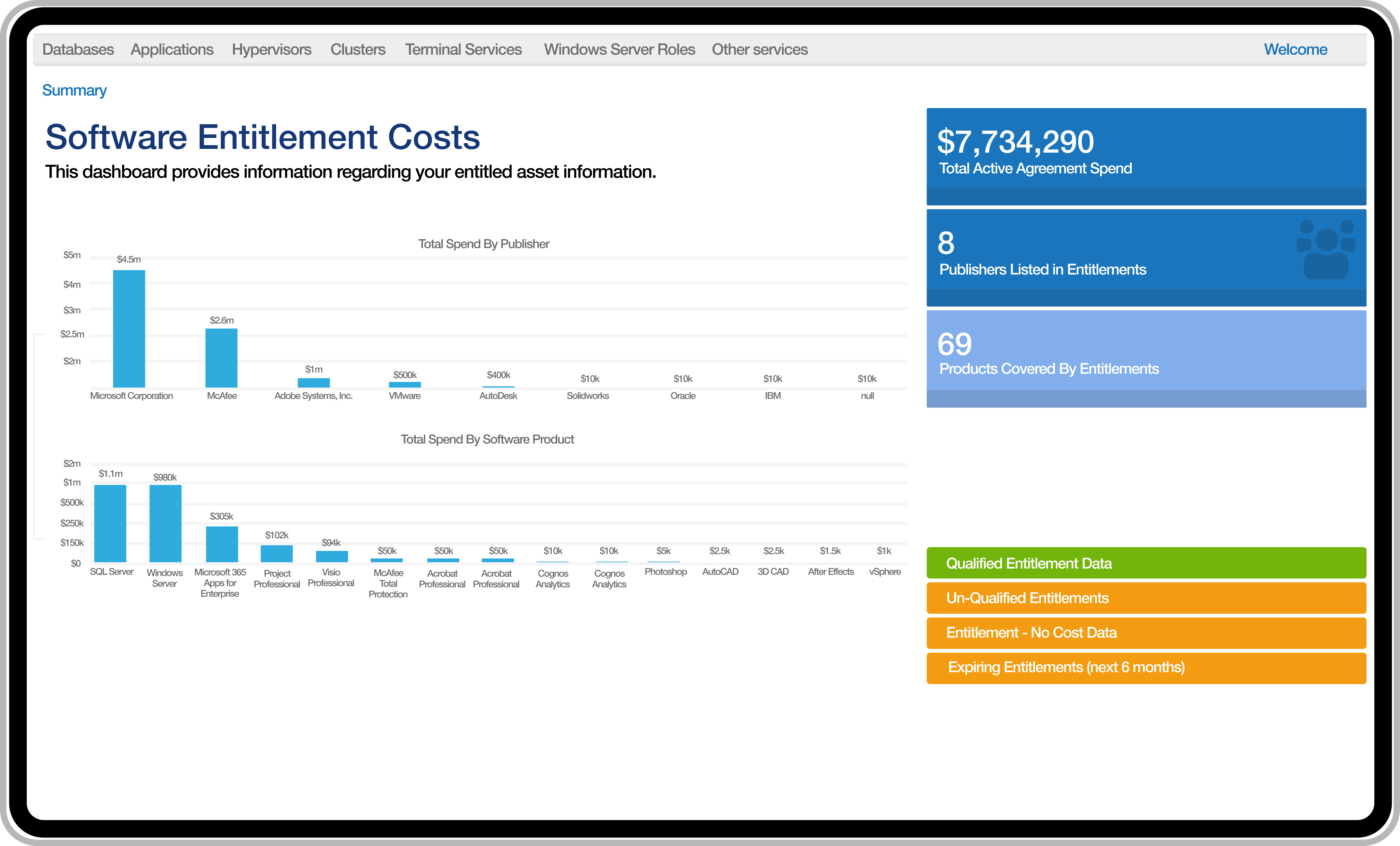
Support software asset management with inventory, entitlements, and license rules
Asset Vision Workstation enables IT to prepare an accurate, thorough, and detailed picture of license compliance without outside vendor involvement, dramatically reducing the complexity and manual tasks required to manage software license entitlement information. It forms the basis for sound Software Asset Management practices and, in conjunction with other tools in the Asset Vision suite, can reduce software expenditure and eliminate compliance risk.
Whether you are reconciling licenses for desktop applications or datacenter software assets, you can compare license assignments to licenses owned to understand the size and scope of your software license compliance risk. Asset Vision incorporates a reporting function that leverages the data view concept to help build pivot views and dashboards. Besides numerous pre-built data views which can be modified and saved to speed report creation custom views can be easily created and shared.
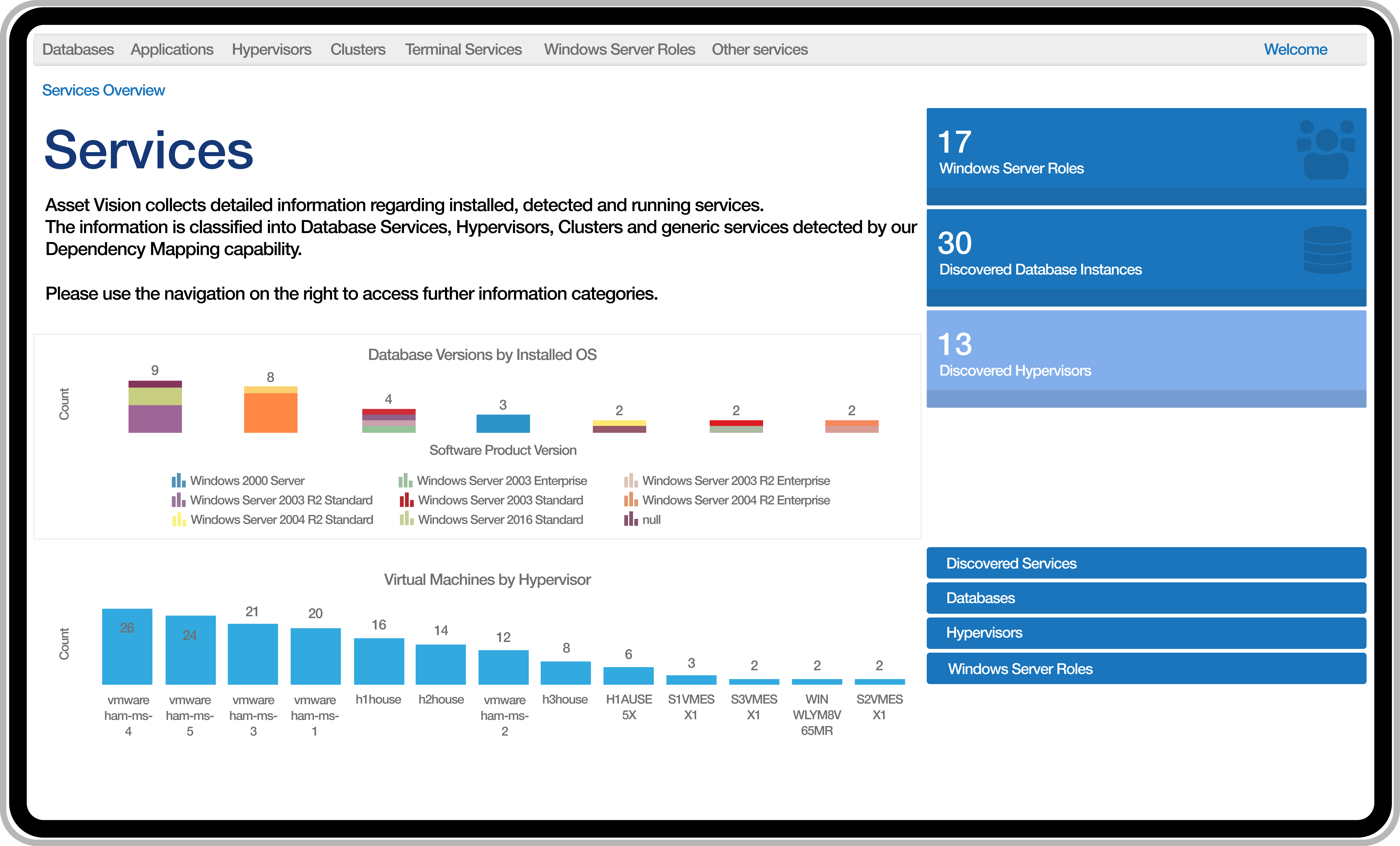
Asset Vision - Server
Asset Vision Server provides the foundational information necessary to support ITSM and IT Operations in even the largest corporations. Maintaining an accurate up-to-date inventory of servers and their associated software is critical to compliance, support and security activities IT must perform.
By having server discovery, inventory and normalization with dependency mapping in a single solution you avoid the need for deploying agents and ensure data is consistent, timely and accurate.
By providing detailed discovery of services within a network Asset Vision provides information on those devices that consume the services and their hosts. As a result, IT service delivery is improved and server rationalization projects can be assured of success.
Dependency mapping
Asset Vision Dependency Mapping operates without an agent, augmenting the agentless server discovery capabilities of Asset Vision. Overlaying dependencies on your asset inventory identifies under and overused servers as well as the software causing the dependency.
See Our Resources
Get started with Scalable
Get in contact with a member of the Scalable team today.