The Importance of Trustworthy Data! Validate and Verify
-
March 21, 2017
- Posted by: Scalable Team
I never guess. It is a capital mistake to theorize before one has data. Insensibly one begins to twist facts to suit theories, instead of theories to suit facts.
— Sir Arthur Conan Doyle, Author of Sherlock Holmes Stories
Hard to argue with this logic, especially in such a data intensive industry as ours. The old adage of ‘Garbage in Garbage out’ is pretty self-explanatory. If we agree it is fundamental to good IT practices, why does it still persist?
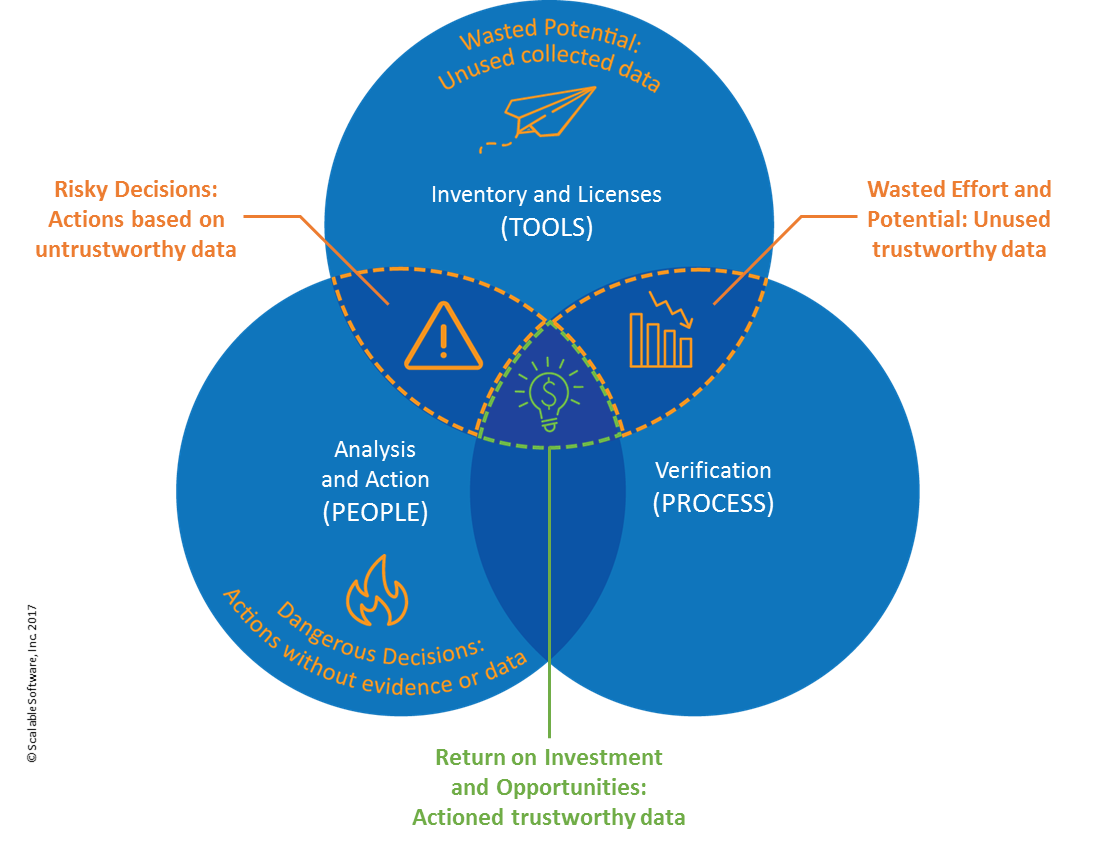
I would suggest that we still do not focus enough on the interplay of people, process and tools. Considering that making decisions on limited or no data is dangerous but making decisions on bad data is worse, this is perplexing. Not only could the outcome be wrong, the source of the data will be called into question. If this is your fledgling SAM program where you are working hard to change the culture and prove your worth, a single incident could ruin your reputation and cause your ‘customers’ to lose all confidence in the program.
The solution is to build confirmation and verification from day one to ensure all data (licenses and inventory) is valid and accurate and more importantly the people and processes are working well together.
 Having good data validation will highlight issues and allow root cause analysis to solve problems before they occur publicly. You may well need to fight for the resources to perform these tasks as they may not appear to have a direct outcome. It’s best to prepare some examples of the impact a failure in this area can have to the bottom line.
Having good data validation will highlight issues and allow root cause analysis to solve problems before they occur publicly. You may well need to fight for the resources to perform these tasks as they may not appear to have a direct outcome. It’s best to prepare some examples of the impact a failure in this area can have to the bottom line.
This graphic highlights and summarizes the risk in not getting this right.
When planning your data validation process don’t overlook these 7 key areas:
- Performing regular snap audits of simple data: For example licenses in your SAM tools versus the source. Quick and often valuable in highlighting issues early.
- Your hardware inventory coverage: You need to know you have for example 95% inventoried and 5% unknowns. Imagine the cost and security risk of 500 additional unmanaged PCs full of software with out of date antivirus software and no patches.
- Check your integrations, connectors and middleware: Don’t assume they are still working and providing good data.
- Your data collection tools: All tools need to be health checked but more so SAM tools which rely on complex and ever changing licensing rules.
- Outsourced IT: Ideally you will have SLAs to define the relationship and process but the responsibility is still yours.
- SaaS: Checking accounts and roles is still key, a rogue account is a cost and security risk.
- Conducting comparison exercises: at least once a year between the outputs of SAM, Discovery, Active Directory, Exchange, Antivirus, HR, and Payroll (yes they will have different numbers). It is a huge task but can uncover a huge range of processes and data issues.
Final thoughts. Use your wonderful data to help the entire business beyond just counting licenses just make sure you aren’t peddling “garbage out.”
Have some top tips or horror stories to share? I would love to hear them.